| What is NATural IP? |
With NATural IP firewall traversal technology you can use VoIP, video-conferencing and all peer-to-peer applications from behind the firewall, without compromising network security.
Stay in control of application usage. No more compromises between security and functionality!
If your network or internet connection uses any of these...
| Shared IP address | |
| Network Address Translation (NAT) | |
| a Firewall of some kind |
... then you have probably found that it causes problems with many kinds of Internet applications.
You need to use programs like NetMeeting
If you are technically minded, you may be able to get around this problem by opening your firewall. But that reduces your network security, which you probably wouldn't want to do.
NATural IP, on the other hand, allows you to run all your existing applications without reducing your network security or requiring individual IP addresses for each PC on your network.
| What is the Benefit? |
Corporations the world over are looking to benefit from the use of the Internet. Software products that facilitate the use of the Internet for purposes such as Video Conferencing, Voice Over IP (VOIP), group collaboration and file sharing are seeing explosive growth in corporate usage.
But security is growing concern with growing threats such as network intruders and terrorism.
NATural IP is a new concept in Internet security. In the past, if you wanted more security, you had to accept less functionality.
NATural IP is our very own technology, developed from scratch by ourselves. We developed it because we found ourselves up against the same "security vs usage" issues that network administrators the world over have to cope with.
It allows you to gain all the security benefits and efficient use of IP addresses that a NAT firewall would normally provide, but WITHOUT the main downside: a general incompatibility with peer-to-peer and streaming media applications.
| How things normally (don't) work? |
The illustration below shows a typical direct peer-to-peer communication between two systems, at various physical locations on the Internet.
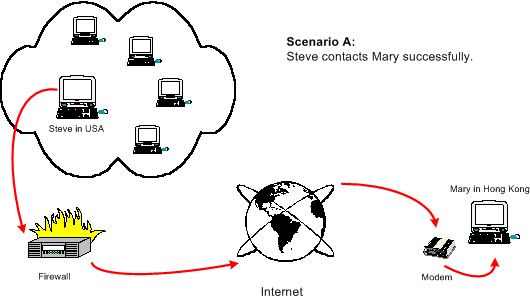
In this example, Steve, who is located in the U.S.A., is communicating with Mary, who is located in Hong Kong. They are using an Internet based video conferencing system (eg Microsoft NetMeeting), which does not require streamed audio/video data to go through a central server.
Steve's system is connected to an office network, which in turn is connected to the Internet through a NAT firewall. Each system on Steve's office network has its own internal IP address, but, because of the NAT firewall, they all share one external IP address.
Mary, however, has her own dial-up connection to the Internet, by means of a modem and regular voice telephone line. Her ISP has allocated a pool of genuine IP addresses to be used by each dial-up user when they are connected. Hence, Mary is fortunate enough to have her own unique IP address when her system is connected to the Internet.
Scenario (a) illustrates what takes place when Steve places a call from his system, over the Internet to Mary's system. Steve's system is able to make a direct peer-to-peer connection to Mary's system, and the call goes through his office network, through the firewall, onto the Internet, and finally to Mary's system through her modem.
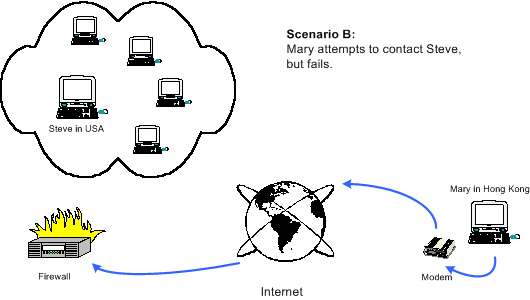
Scenario (b) illustrates what takes place when Mary attempts to place a call from her system over the Internet to Steve's system. As all of the systems on Steve's office network share one external IP address, it is not possible for Mary's system to make a direct peer-to-peer connection with Steve's system. This is because Mary's system only "sees" Steve's external IP address, which in reality is just the IP address of the NAT firewall. The firewall has no way of knowing which system on Steve's network the connection should be forwarded to, so the file transfer fails. Most video conferencing systems would simply give up at this point, and Mary would see an error message stating that Steve's system was not able to accept her call.
Although the scenario here has used video conferencing applications as an example, the same problems would occur with other types of peer-to-peer application.